Big 4security conferences), IEEE Communications Magazine (impact factor 11.2), best paper candidate CNS'20, etc. Previously, I was an industrial Postdoctoral Fellow at University of Waterloo collaborating with Ericsson Montreal. I completed my PhD at Concordia University (with Prof. Lingyu Wang and Prof. Makan Pourzandi), when I was collaborating with Ericsson on NSERC/Ericsson IRC in SDN/NFV Security Project.
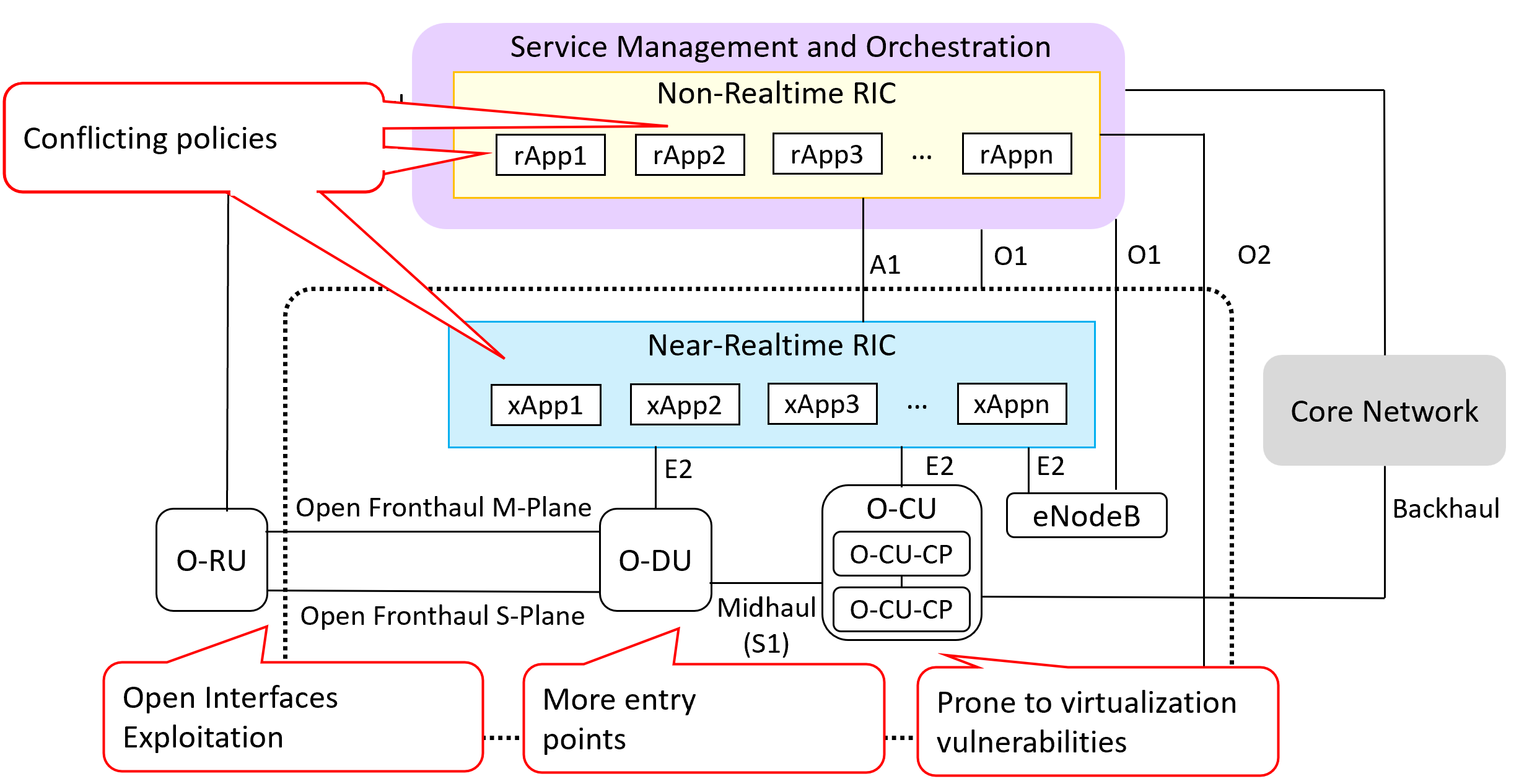
ProvTalk: Towards Interpretable Multi-level Provenance Analysis in Networking Functions Virtualization (NFV)
Azadeh Tabiban, Heyang Zhao, Yosr Jarraya, Makan Pourzandi, Mengyuan Zhang and Lingyu Wang
Proc. the Network and Distributed System Security Symposium (NDSS 2022) (Acceptance ratio 16.2%)
PDF Slides Talk
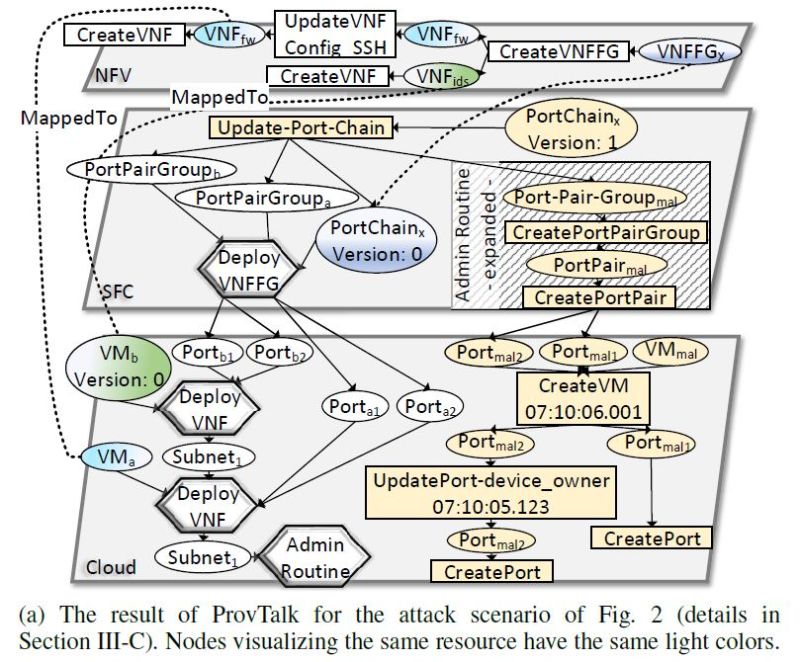
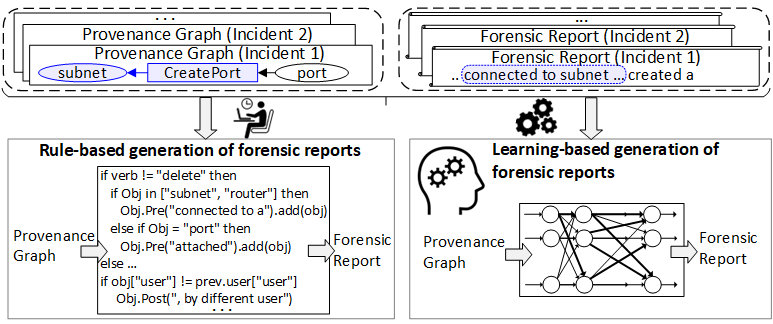
Catching Falling Dominoes: Cloud Management-Level Provenance Analysis with Application to OpenStack
Azadeh Tabiban, Yosr Jarraya, Mengyuan Zhang, Makan Pourzandi, Lingyu Wang and Mourad Debbabi
Proc. the 8th IEEE Conference on Communications and Network Security (CNS 2020)
PDF Slides Demo
Selected as a best paper candidate
PERMON: An OpenStack Middleware for Runtime Security Policy Enforcement in Clouds
Azadeh Tabiban, Suryadipta Majumdar, Lingyu Wang and Mourad Debbabi
Proc. the 4th IEEE Workshop on Security and Privacy in the Cloud (SPC 2018)
PDF Demo
Proactivizer: Transforming Existing Verification Tools into Efficient Solutions for Runtime Security Enforcement
Suryadipta Majumdar, Azadeh Tabiban, Meisam Mohammady, Alaa Oqaily, Yosr Jarraya, Makan Pourzandi, Lingyu Wang and Mourad Debbabi
Proc. the 24th European Symposium on Research in Computer Security (ESORICS 2019)
PDF
Learning Probabilistic Dependencies among Events for Proactive Security Auditing in Clouds
Suryadipta Majumdar, Azadeh Tabiban, Yosr Jarraya, Momen Oqaily, Amir Alimohammadifar, Makan Pourzandi, Lingyu Wang and Mourad Debbabi
Journal of Computer Security (JCS), Vol. 27, No. 2, March 2019, pages 165-202
PDF
Multi-Level Proactive Security Auditing for Cloud
Suryadipta Majumdar, Azadeh Tabiban, Meisam Mohammady, Alaa Oqaily, Yosr Jarraya, Makan Pourzandi, Lingyu Wang and Mourad Debbabi
Proc. the IEEE Conference on Dependable and Secure Computing (DSC 2019), Hangzhou, China, November 18-20, 2019
Cloud Security Auditing (Book)
Suryadipta Majumdar, Taous Madi, Yushun Wang, Azadeh Tabiban, Momen Oqaily, Amir Alimohammadifar, Yosr Jarraya, Makan Pourzandi, Lingyu Wang and Mourad Debbabi
Springer, 2019, ISBN 978-3-030-23127-9
